A massive ransomware attack, reportedly leveraging a hacking tool from the National Security Agency, is spreading worldwide, including major medical centers. US Government officials report as many as 300,000 computers were infected (up from 75,000 computers on Friday) worldwide as of 7pm May 13 according to reports.
The ransomware, which encrypts data on hard drives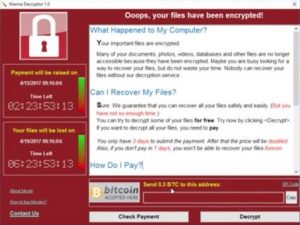 until payment is received, struck the National Health Service in the UK, a telecommunications firm in Spain and FedEx.
until payment is received, struck the National Health Service in the UK, a telecommunications firm in Spain and FedEx.
Nicknamed WannaCry or Wanna Decryptor, the ransomware exploits bugs in how Window Operating Systems share files. Microsoft provided fixes to secure the Server Message Block 1.0 (a.k.a. SMBv1) protocol targeted by the attack months prior but those infected did not update their systems in time.
WHAT IS THE DANGER?
The risk of the attack that started last week was limited because a “kill switch” was luckily found and most of the computers in the US were able to be patched. However, hospitals in London had to delay some surgeries because patient records were compromised and encrypted. While we may have dodged a bullet this time, cybercriminals have already fired off a more virulent attack and more are predicted.
WHAT CAN YOU DO TO PREVENT THIS ATTACK?
“Obviously timely patching is critical.” advises Dr. Billy Willis, Chief Technology Officer of Duke University Health.
Alert your IT staff immediately of the potential threat.
They should already have:
- enforced strong passwords
- restricted internet usage
- rolling backups of computers
- Restricted access to only work related websites
- installed & properly configured antivirus, firewalls, routers
- and other basic security practices.
Your staff should have been trained to ignore or verify before opening suspicious emails and email attachments; even the sender’s name and email address can be spoofed.
Dr. Ravi Goel from Wills Eye Hospital and other experts gave advice to the American Academy of Ophthalmology just weeks before the attack. See https://www.aao.org/practice-management/article/protecting-your-practice-ransomware-cyberthreats for the details.
You can also have your IT professional remove the use or support of SMBv1 CIFS File Sharing support. But make certain you test the system thoroughly to reduce the chances of unwanted side effects.
We recommend you verify that backups of all data and critical systems have been performed on all computers and servers and patches on all Windows systems have been applied to close the vulnerability.
Go to your Windows Update system application or visit Microsoft’s Windows Support page to apply the latest updates.
HOW DO I PROTECT SYSTEMS NO LONGER SUPPORTED?
Imaging and other systems, including those that run retina cameras and OCTs, often have computers attached or embedded within the device. The computers will have an operating system like Windows or Linux to manage and run the software required to drive the device. While those that run Linux are immune to this particular attack, those that run Windows Server 2003 or even older, surprisingly still common, operating systems like Windows XP are especially vulnerable if connected to the network or the internet.
See if your TopCon retina camera is especially vulnerable
Dr. Willis, who also served as Deputy CIO of the State of North Carolina explains that to attackers, “visibility from outside is critical. Systems that cannot be patched or are no longer supported should [only] be very specifically visible on the network.” Dr. Willis continues, “these systems should be used for their intended purpose only.” He warns “web surfing, email use, etc. from these systems bring much more vulnerability.”
These older systems may need to be disconnected from any networks in the short term until solutions can be found and the internet access should be removed completely as a general rule.
“If these systems are critical to your operation, there are ways to protect them and shield them from attacks without removing them from service.” Sidd Chopra, President of Analytrix, advises. “We’ve proven that you can keep your legacy equipment safe and operational for years past their life expectancy. But everything begins with isolating the equipment and backing up everything”
Moving forward, “we all need think about how we may eliminate the use of file systems as data repositories.” Dr. Willis concludes.
WHAT CAN YOU DO IF YOU ARE A VICTIM OF AN ATTACK?
First, alert your IT staff immediately and call a professional and then consider your options.
- See if your antivirus software can block it (up to date protection software may work 30% of the time)
- Restore from back up (if they were done correctly)
- Pay the ransom ( experts don’t recommend paying the ransom as most still don’t get the data back. But that isn’t always the case )
You will also need to figure in any disruption to the organization in the costs.
WHAT HAPPENS IF I JUST IGNORE THE THREAT?
In the case of ransomware, the attackers encrypt data and other files and you and your systems will no longer have access to them.
![wannacrypt-ransom-note-100722688-large[1]](http://www.analytrix.com/wp-content/uploads/2017/05/wannacrypt-ransom-note-100722688-large1-e1494885983934-300x134.jpg)
This may be of little consequence or it could be catastrophic, depending on the importance of the data and how old your backups are.
If they get access to employee, financial or patients medical records, the costs can skyrocket. The attackers can sell the data on the black market exposing you and your company to fines, litigation and identity theft claims.
HOW DOES IT SPREAD?
“WannaCry works differently than many past ransomware attacks because of the way it spreads through networks” according to Matt Hamblen, senior editor at ComputerWorld. “After an unknowing worker clicks on a compressed Zip attachment to launch WannaCry, it can spread through a corporate network to infect and lock other computers — even those where no link or attachment was accessed.” he continues.
BOTTOM LINE?
Like it or not, we live in a world with bad actors.
If you have something work stealing, you are vulnerable.
And patient data is worth stealing.
Having spending years doing IT security audits for Fortune 100 companies, Chopra explains “Cyber criminals are relentless opportunists; they design systems to test every window and try every door. They look for the easiest way to get the most amount of money.”
“Unfortunately, it looks like they have decided medical offices are worth their time.” he laments. “No one is benefits if you are easy pickings. Except for the criminals.”
